准备ubuntu 服务器,支持ipv6
服务器信息查询
ip a
查询ipv6 地址例如:2a01:4ff:f0:c03a::1/64
查询网卡名称:eth0
生成多条ipv6工具
https://www.bulianglin.com/archives/ipv6.html
- 生成ipv6
- 生成shell命令
到服务器中执行
ipv6保存成永久文件
查看文件名
ls /etc/netplan/
打开编辑(将文件名替换成真实的文件名字.yaml)
cd /etc/netplan/01-netcfg.yaml
修改文件格式
修改文件后执行
sudo netplan try
回车
sudo netplan apply
查看ip状态
ip addr show eth0
搭建Vmess梯子
1. 远程下载Vmess方案
更新系统包索引
sudo apt update && sudo apt upgrade -y
安装必要的工具
sudo apt install wget curl -y
下载脚本
curl -O https://raw.githubusercontent.com/bulianglin/demo/main/xrayL.sh
2. 本地创建Vmess脚本
nano xrayL.sh
Vmess脚本
DEFAULT_START_PORT=20000 #默认起始端口
DEFAULT_SOCKS_USERNAME="userb" #默认socks账号
DEFAULT_SOCKS_PASSWORD="passwordb" #默认socks密码
DEFAULT_WS_PATH="/ws" #默认ws路径
DEFAULT_UUID=$(cat /proc/sys/kernel/random/uuid) #默认随机UUID
IP_ADDRESSES=($(hostname -I))
install_xray() {
echo "安装 Xray..."
apt-get install unzip -y || yum install unzip -y
wget https://github.com/XTLS/Xray-core/releases/download/v1.8.3/Xray-linux-64.zip
unzip Xray-linux-64.zip
mv xray /usr/local/bin/xrayL
chmod +x /usr/local/bin/xrayL
cat <
[Unit]
Description=XrayL Service
After=network.target
[Service]
ExecStart=/usr/local/bin/xrayL -c /etc/xrayL/config.toml
Restart=on-failure
User=nobody
RestartSec=3
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable xrayL.service
systemctl start xrayL.service
echo "Xray 安装完成."
}
config_xray() {
config_type=$1
mkdir -p /etc/xrayL
if [ "$config_type" != "socks" ] && [ "$config_type" != "vmess" ]; then
echo "类型错误!仅支持socks和vmess."
exit 1
fi
read -p "起始端口 (默认 $DEFAULT_START_PORT): " START_PORT
START_PORT=${START_PORT:-$DEFAULT_START_PORT}
if [ "$config_type" == "socks" ]; then
read -p "SOCKS 账号 (默认 $DEFAULT_SOCKS_USERNAME): " SOCKS_USERNAME
SOCKS_USERNAME=${SOCKS_USERNAME:-$DEFAULT_SOCKS_USERNAME}
read -p "SOCKS 密码 (默认 $DEFAULT_SOCKS_PASSWORD): " SOCKS_PASSWORD
SOCKS_PASSWORD=${SOCKS_PASSWORD:-$DEFAULT_SOCKS_PASSWORD}
elif [ "$config_type" == "vmess" ]; then
read -p "UUID (默认随机): " UUID
UUID=${UUID:-$DEFAULT_UUID}
read -p "WebSocket 路径 (默认 $DEFAULT_WS_PATH): " WS_PATH
WS_PATH=${WS_PATH:-$DEFAULT_WS_PATH}
fi
for ((i = 0; i < ${#IP_ADDRESSES[@]}; i++)); do
config_content+="[[inbounds]]\n"
config_content+="port = $((START_PORT + i))\n"
config_content+="protocol = \"$config_type\"\n"
config_content+="tag = \"tag_$((i + 1))\"\n"
config_content+="[inbounds.settings]\n"
if [ "$config_type" == "socks" ]; then
config_content+="auth = \"password\"\n"
config_content+="udp = true\n"
config_content+="ip = \"${IP_ADDRESSES[i]}\"\n"
config_content+="[[inbounds.settings.accounts]]\n"
config_content+="user = \"$SOCKS_USERNAME\"\n"
config_content+="pass = \"$SOCKS_PASSWORD\"\n"
elif [ "$config_type" == "vmess" ]; then
config_content+="[[inbounds.settings.clients]]\n"
config_content+="id = \"$UUID\"\n"
config_content+="[inbounds.streamSettings]\n"
config_content+="network = \"ws\"\n"
config_content+="[inbounds.streamSettings.wsSettings]\n"
config_content+="path = \"$WS_PATH\"\n\n"
fi
config_content+="[[outbounds]]\n"
config_content+="sendThrough = \"${IP_ADDRESSES[i]}\"\n"
config_content+="protocol = \"freedom\"\n"
config_content+="tag = \"tag_$((i + 1))\"\n\n"
config_content+="[[routing.rules]]\n"
config_content+="type = \"field\"\n"
config_content+="inboundTag = \"tag_$((i + 1))\"\n"
config_content+="outboundTag = \"tag_$((i + 1))\"\n\n\n"
done
echo -e "$config_content" >/etc/xrayL/config.toml
systemctl restart xrayL.service
systemctl --no-pager status xrayL.service
echo ""
echo "生成 $config_type 配置完成"
echo "起始端口:$START_PORT"
echo "结束端口:$(($START_PORT + $i - 1))"
if [ "$config_type" == "socks" ]; then
echo "socks账号:$SOCKS_USERNAME"
echo "socks密码:$SOCKS_PASSWORD"
elif [ "$config_type" == "vmess" ]; then
echo "UUID:$UUID"
echo "ws路径:$WS_PATH"
fi
echo ""
}
main() {
[ -x "$(command -v xrayL)" ] || install_xray
if [ $# -eq 1 ]; then
config_type="$1"
else
read -p "选择生成的节点类型 (socks/vmess): " config_type
fi
if [ "$config_type" == "vmess" ]; then
config_xray "vmess"
elif [ "$config_type" == "socks" ]; then
config_xray "socks"
else
echo "未正确选择类型,使用默认sokcs配置."
config_xray "socks"
fi
}
main "$@"
赋予脚本执行权限
chmod +x xrayL.sh
运行脚本
bash xrayL.sh
示例:
选择生成的节点类型 (socks/vmess): vmess
起始端口 (默认 20000): 42000
UUID (默认随机):
WebSocket 路径 (默认 /ws): /wss
复制链接地址:选中链接Ctrl+c
开启BBR
创建文件
nano enable_bbr.sh
粘贴脚本
#!/bin/bash
# 检查是否以 root 权限运行
if [ "$EUID" -ne 0 ]; then
echo "请以 root 权限运行此脚本:sudo $0"
exit 1
fi
# 颜色输出函数
green() { echo -e "\033[32m$1\033[0m"; }
red() { echo -e "\033[31m$1\033[0m"; }
yellow() { echo -e "\033[33m$1\033[0m"; }
# 检查内核版本
KERNEL_VERSION=$(uname -r | cut -d'.' -f1-2)
MIN_KERNEL="4.9"
if [ "$(printf '%s\n' "$MIN_KERNEL" "$KERNEL_VERSION" | sort -V | head -n1)" != "$MIN_KERNEL" ]; then
red "当前内核版本 ($KERNEL_VERSION) 低于 4.9,无法启用 BBR"
yellow "请升级内核后重试,建议使用 'sudo apt install linux-generic-hwe-22.04' 或手动安装新内核"
exit 1
else
green "内核版本 ($KERNEL_VERSION) 符合要求,继续配置 BBR"
fi
# 检查是否已启用 BBR
CURRENT_CONGESTION=$(sysctl -n net.ipv4.tcp_congestion_control)
if [ "$CURRENT_CONGESTION" == "bbr" ]; then
green "BBR 已启用,无需重复配置"
exit 0
fi
# 修改 sysctl 配置
SYSCTL_FILE="/etc/sysctl.conf"
BBR_CONFIG="net.core.default_qdisc=fq\nnet.ipv4.tcp_congestion_control=bbr"
# 备份原配置文件
if [ ! -f "$SYSCTL_FILE.bak" ]; then
cp "$SYSCTL_FILE" "$SYSCTL_FILE.bak"
green "已备份原配置文件到 $SYSCTL_FILE.bak"
fi
# 添加 BBR 配置
grep -q "net.ipv4.tcp_congestion_control" "$SYSCTL_FILE"
if [ $? -eq 0 ]; then
sed -i '/net.core.default_qdisc/d' "$SYSCTL_FILE"
sed -i '/net.ipv4.tcp_congestion_control/d' "$SYSCTL_FILE"
echo -e "$BBR_CONFIG" >> "$SYSCTL_FILE"
else
echo -e "$BBR_CONFIG" >> "$SYSCTL_FILE"
fi
# 应用配置
sysctl -p > /dev/null
green "BBR 配置已写入并应用"
# 验证 BBR 是否启用
NEW_CONGESTION=$(sysctl -n net.ipv4.tcp_congestion_control)
if [ "$NEW_CONGESTION" == "bbr" ]; then
green "BBR 已成功启用!"
echo "当前 TCP 拥塞控制算法:$NEW_CONGESTION"
echo "可用算法:$(sysctl -n net.ipv4.tcp_available_congestion_control)"
else
red "BBR 启用失败,请检查系统配置"
yellow "当前算法:$NEW_CONGESTION"
exit 1
fi
# 提示重启(可选)
yellow "配置已生效,通常无需重启。如需确保完全应用,可运行 'sudo reboot'"
BBR脚本文件授权
chmod +x enable_bbr.sh
BBR脚本运行
sudo ./enable_bbr.sh
批量生成ipv6多端口文件
https://www.bulianglin.com/archives/ipv6.html#startnum
- 起始端口:42000
- 结束端口:(根据数量需要,不要超过42100)
到此:软路由可以直接导入监听端口即可,V2ray继续下面的步骤
批量订阅转换成Clash文件
源地址:https://github.com/tindy2013/subconverter/releases
window 64位直接下载链接:https://github.com/tindy2013/subconverter/releases/download/v0.9.0/subconverter_win64.7z
程序本地地址:
E:\A2023 所有网站文件\subconverter_win64\subconverter\subconverter.exe
双击可运行文件不要关闭
将批量生成的ipv6文件粘贴到
https://bulianglin.com/archives/51.html#pagewrap
将生成的文件全选复制
批量生成适合监听的v2ray+clash meta分流的socks5代理文件
https://www.bulianglin.com/archives/tosocks.html#inputYAML
下载保存
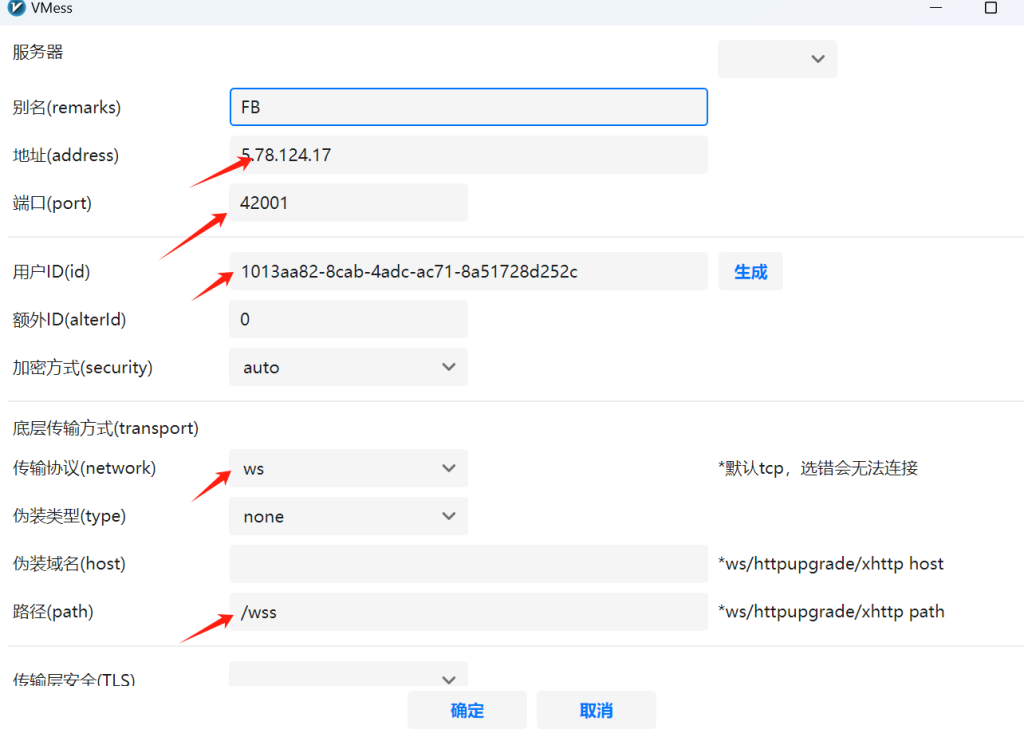
配置V2rayN
需要支持:clash meta 或者 mihomo
V2ray下载链接: https://github.com/2dust/v2rayN/releases/download/7.10.4/v2rayN-windows-64-desktop.zip
服务器 – 添加自定义配置服务器
别名:随意
地址:保存的文件
core类型:clash meta 或者 mihomo
socks端口:随意填写 类如123456(一定要填写)
配置指纹浏览器
查看节点配置信息
cat /etc/xrayL/config.toml